Incident Management
A working group consisting of University of Chicago stakeholders and industry experts was established to develop an Incident Management/Incident Response (IR) program to automate the process for tracking and reporting on cybersecurity incidents within the Biological Sciences Division (BSD). The automation capabilities within the program provides automated notifications to key stakeholders within the IR program as incidents are tracked and remediated. The workflow requires manual human intervention to validate that appropriate approvals are acquired before remediation activities occur.
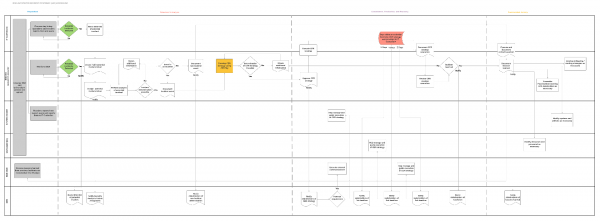
All Potential Security Events fall into the Incident Response Workflow (see below), which relies on NIST 800-61r2: Computer Security Incident Handling Guide (National Institute of Standards and Technology, NIST), which uses 4 phases of Incident Response: Preparation, Detection and Analysis, Containment/Eradication/Remediation (CER), and Post-Incident Analysis.
CER Strategies
Containment, Eradication, Remediation (CER) is the strategy or play BSD utilizes in order to combat against specific types of Incidents. Each play is fully documented in the Cybersecurity Incident Response Manual. However, we have provided the following Cheat Sheets in order to provide a more concise document for an IT Custodian to follow in order to address an Incident in a more timely manner.
Training Documents
Cybersecurity Incident Response Manual
Incident Management – IT Custodian Training (*Click on the link and log into the IT GRC Tool with your CNet credentials. Once in the IT GRC tool, click on the Comments to find the training slides.)
Lost/Stolen Device Cheat Sheet
Frequently Asked Questions
Q1. What is a security incident?
A1. A security incident is a violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices. Incidents are typically identified through the continual review and analysis of events. The BSD ISO will determine an event is an incident if the event affects the security (i.e. Confidentiality, Integrity, and/or Availability) of an IT system.
Q2. How is a security incident identified?
A2. During the Detection and Analysis phase, a potential incident event has been observed and reported to the BSD Information Security Office. The BSD Security Analyst gathers information related to the event to make a determination whether the observed event should be classified as an incident. If enough evidence exists to classify the event as an incident, the Security Analyst will work with the appropriate IT Custodians assigned to the affected systems in order to develop a valid Containment, Eradication, and Recovery (CER) strategy.
Q3. What are the IT Custodians expectations during the Incident Response (IR) program?
A3. The IT Custodian has the following responsibilities during the IR program.
1) Reporting Responsibility–As a contributor to the BSD IR process, it is expected that potential incidents are reported to the BSD ISO as soon as possible. If unsure whether, a suspicious event meets the threshold for reporting please contact the BSD ISO for clarity.
2) Expected Support–It Custodians are an integral role within the BSD IR Workflow. It is through the IT Custodian that Security Analyst are able to properly investigate incidents and later remediate these incidents. IT Custodians will be contacted by Security Analysts at several points throughout the IR Workflow. it is expected that the IT Custodian will contribute to the investigation by:
- Answering information requests from the Security Analyst
- Executing assigned tasks within the CER strategy
- Documenting CER execution progress and lessons learned within the GRC